Before Anyone Else
Get the perfect shipping option for you!




Get started for free and Save up to 89%.
The Gloship,
All-In-One
Own your shipping data!
Dashboard

Easy to print!
Labels

Don't worry about your packages
Claim

Want to see all of your reports?
Reports

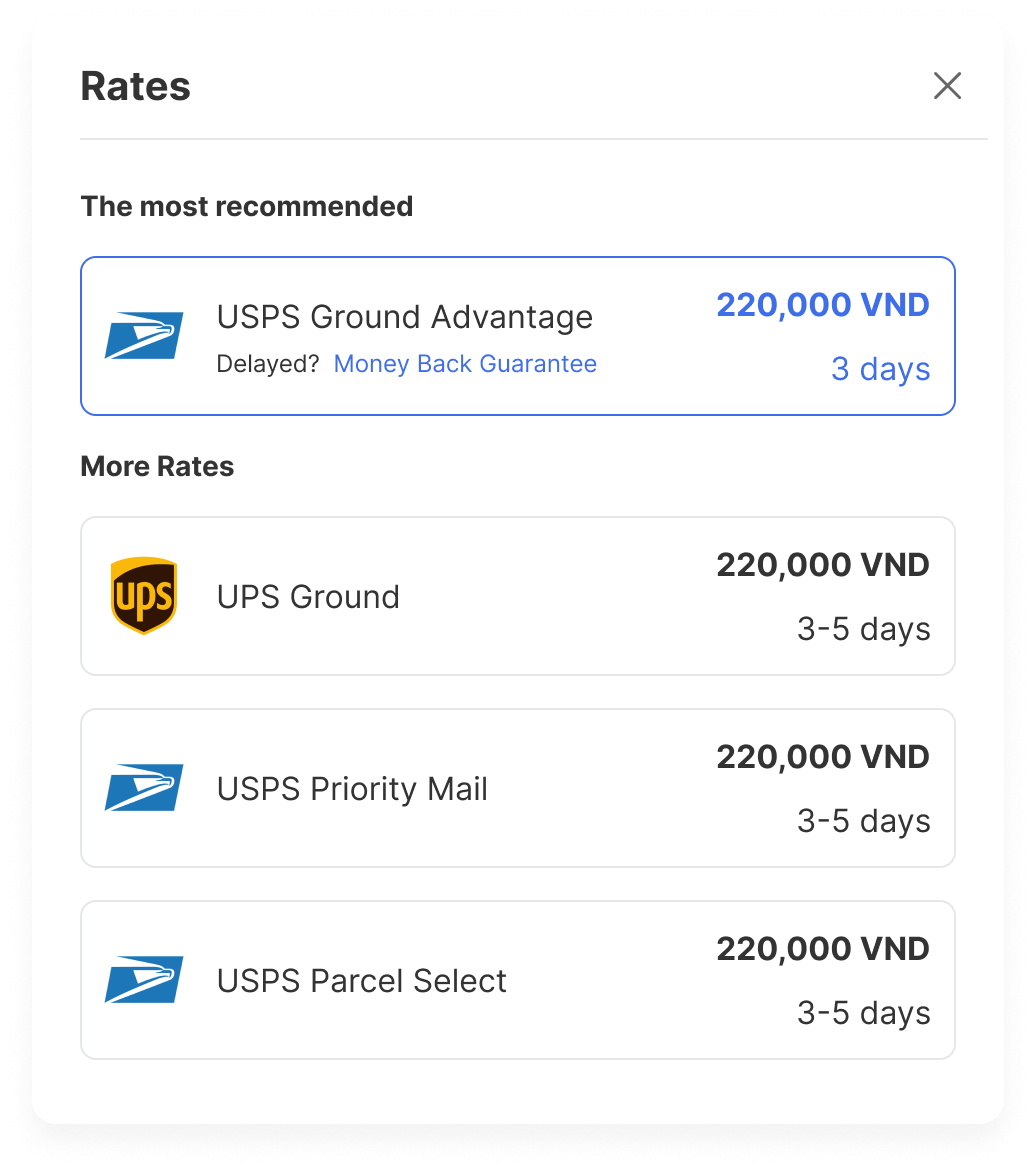
Proactively,
Optimized Shipping Creation
Optimized Shipping Creation




Gloship offers a list of rates from top-tier carriers, including USPS, UPS, FedEx, and DHL, for your packages, allowing you to access discounted rates of up to 89% at a glance. Choose the rate that suits you best!
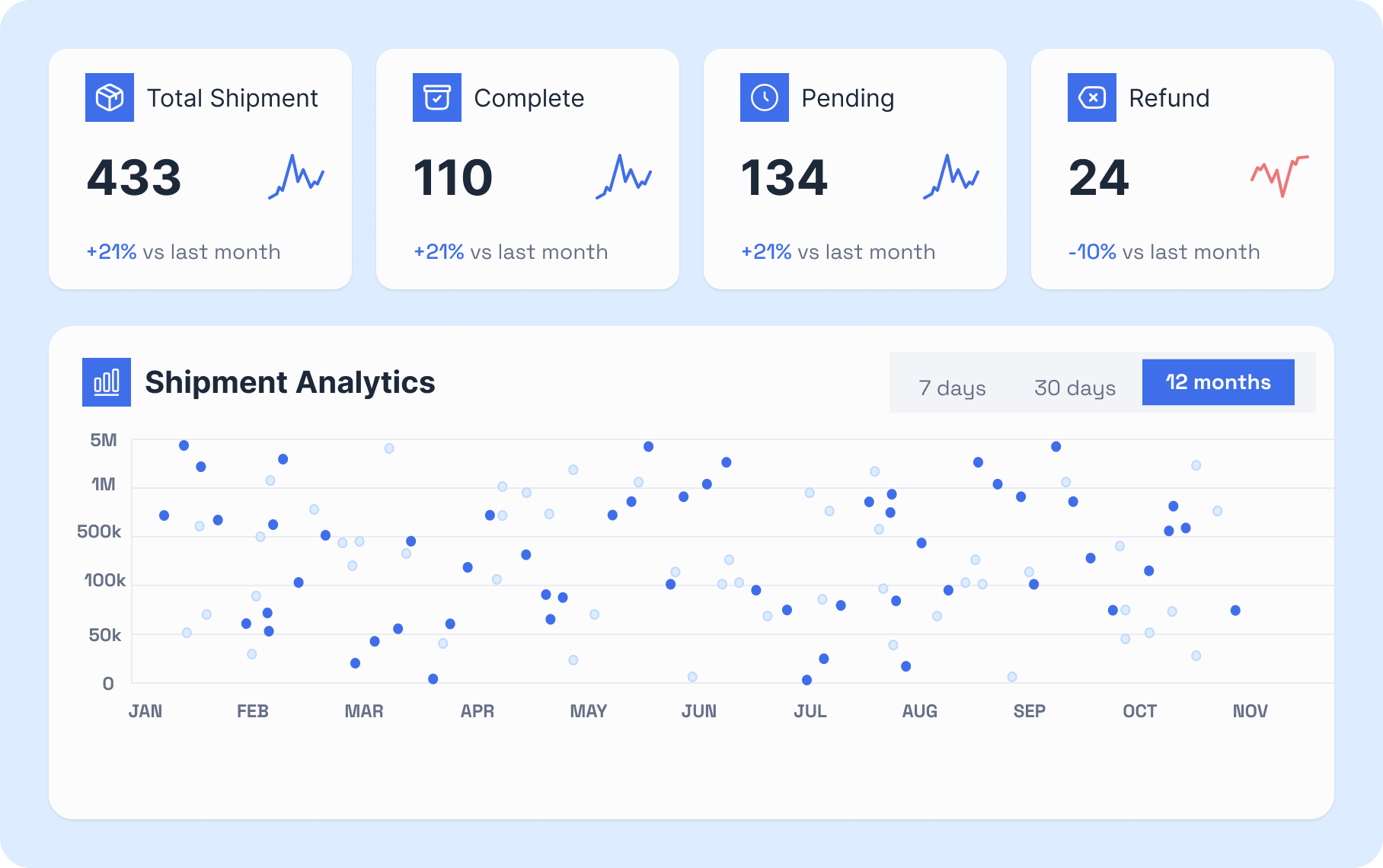
Analytically,
Understand your Shipping at a Glance
Understand your Shipping at a Glance
Our dashboard analytics can help uncover patterns, trends, and relationships that might not be apparent from a single data source, leading to better analysis and decision-making.
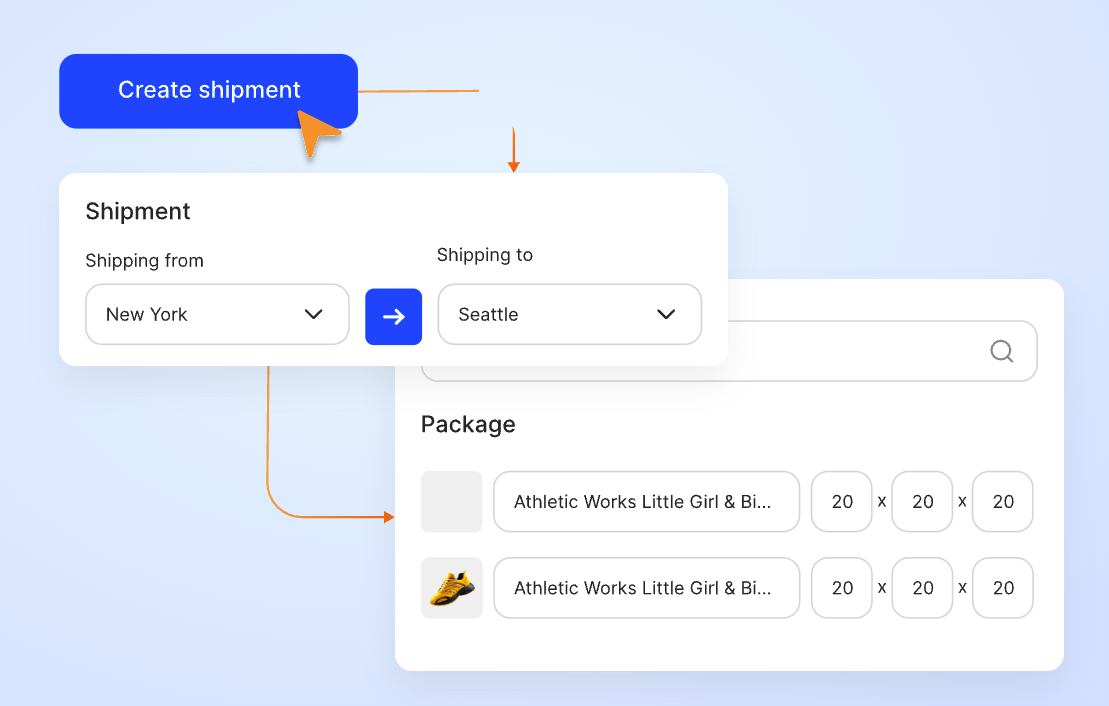
Effortlessly,
Simplify Your Shipping Process with Flexible Tools
Simplify Your Shipping Process with Flexible Tools
Gloship provides a variety of features that help you manage your orders effortlessly. Filter and batch your orders, export shipment reports, file claims for lost or damaged packages, and more!
How It Works
Start in 4 Simple Steps to simplify your shipping process
1. Setup warehouse
Create your origin location to determine shipping zone for each shipment.
2. Top up
Go to wallet and recharge it with the suitable method before purchasing labels.
3. Create Shipment
Access discounted rates from top carriers and select the best option for every shipment.
4. Print Labels & Ship
Print labels, send tracking info to customers, and automatically sync details back to .
How We Protect
Your Security, Our Priority
Authorization
Role-Based Access Control (RBAC): Restricts access to certain parts of the application based on the user's role (e.g., admin, user).
Input Validation
Sanitization: Ensure that user inputs are sanitized to prevent SQL injection, cross-site scripting (XSS), and other injection attacks.
Encryption
HTTPS/SSL: Encrypts data in transit between the user's browser and the web server, preventing eavesdropping and man-in-the- middle attacks. Data Encryption at Rest:…
Session Management
Secure Cookies: Ensure cookies are flagged as Secure (transmitted over HTTPS only) and HttpOnly (not accessible via JavaScript) to prevent theft. Session Timeout: Automaticall…
Error Handling and Logging
Detailed Error Messages: Ensure that error messages do not reveal sensitive information that could aid an attacker. Audit Logs: Maintain detailed logs of user activity, including failed…
Data Protection
Data Backup and Recovery: Regularly back up data and have a plan for recovering from data loss or corruption.
Compliance and Best Practices
Regular Security Audits: Perform regular code reviews to identify and address vulnerabilities Compliance with Standards: Ensure the application complies with relevant security…

Our Privacy Policy
Learn more about how we safeguard your data.
Enjoy massive discounts from top carriers

